OIDC SSO Pro Business
Plane enables custom SSO via any identity provider with an official and supported implementation of OIDC standards. This page cites examples from Okta, but we will soon publish provider-specific instructions in phases.
OIDC
You will need to configure values on your IdP first and then on Plane later.
On your preferred IdP
Create a Plane client or application per your IdP's documentation and configure ↓.
TIP
domain.tld is the domain that you have hosted your Plane app on.
| Config | Key |
|---|---|
| Origin URL | http(s)://domain.tld/auth/oidc/ |
| Callback URL | http(s)://domain.tld/auth/oidc/callback/ |
| Logout URL | http(s)://domain.tld/auth/oidc/logout/ |
On Plane
Go to /god-mode/authentication/oidc on your Plane app and find the configs ↓.
TIP
Your IdP will generate some of the following configs for you. Others, you will specify yourself. Just copy them over to each field.
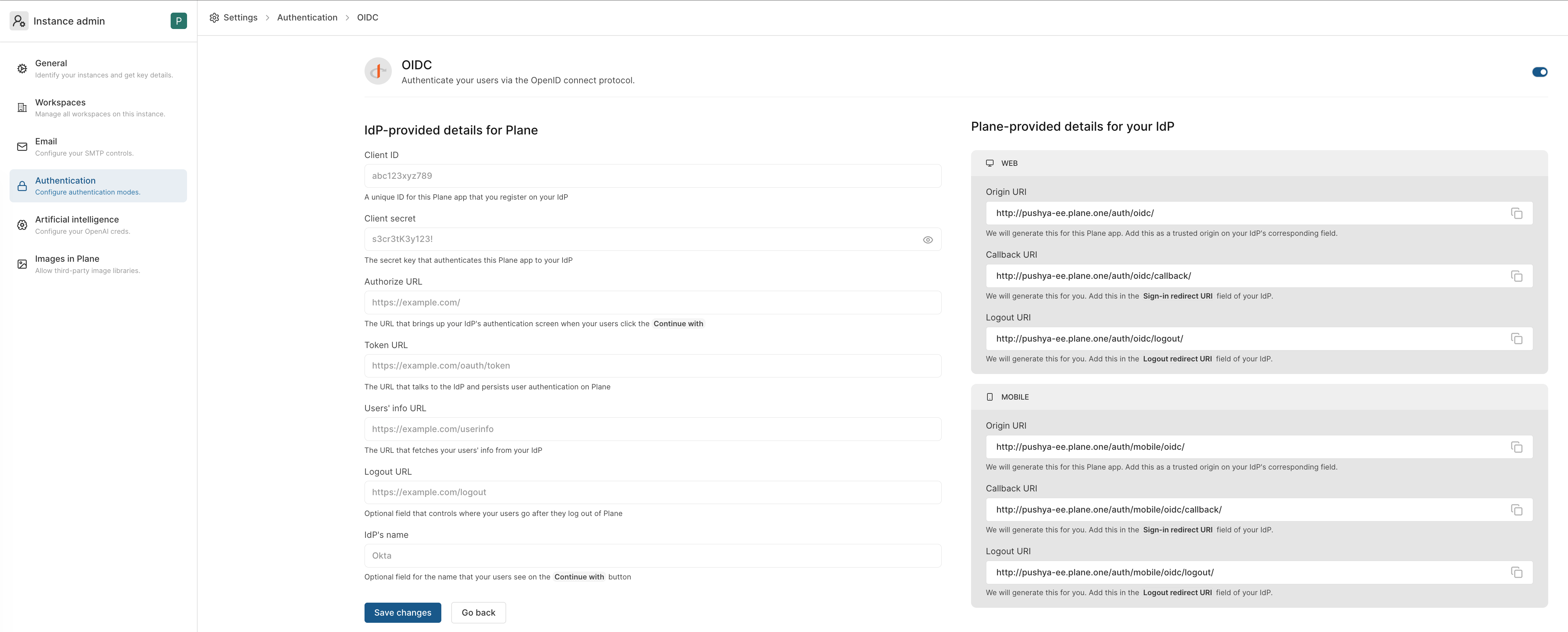
Copy the
CLIENT_IDfor the Plane client or app you just created over from your IdP and paste it in the field for it.With providers like Keycloak, you have to choose a unique ID per app your configure. With providers like Okta and Auth0, you copy over the generated ID over to Plane. Typically, you will find it on the Plane application Home or Settings page on your IdP.
Copy the
CLIENT_SECRETfor the Plane client or app you created over from your IdP and paste it in the field for it.The secret is usually auto-generated and you just need to copy it over from the Plane app or client's Home or Settings page.
Copy the
TOKEN URLfrom your IdP and paste it into the field for it on/god-mode/authentication/oidc/.
Typically used to maintain user authentication and to persist it with refreshes, this URL lives in the.well-known/directory for the Plane app or client on your IdP.Copy the
User info URLfrom your IdP and paste it into the field for it on/god-mode/authentication/oidc/.Used to get an authenticating user's information from the IdP. Plane requires the
emailfield for user authentication. Thefirst_nameandlast_namefields are optional but recommended for a complete user profile. This URL can be copied from the.well-known/directory.Copy the
Authorize URLover from the.well-known/directory and paste it into the field for it on Plane's/god-mode/authentication/oidc/.
This is the URL that Plane's login screen redirects to when your users clickSign up with <name of IDP>orLogin with <name of IdP>.
To test if this URL is right, see if clicking the
Login with <name of your IdP>button brings up your IdP's authentication screen.
Finally, choose a name for your IdP on Plane so you can recognize this set of configs.

